Fresh Install
This page includes a very brief overview of Webmin module screens, before turning the instance into a Tier-2 service stack. The page is going to grow and expand as feedback comes in for better, more detailed explanations. If you are already familiar with Webmin, or you do not wish to use it you may skip this page entirely.
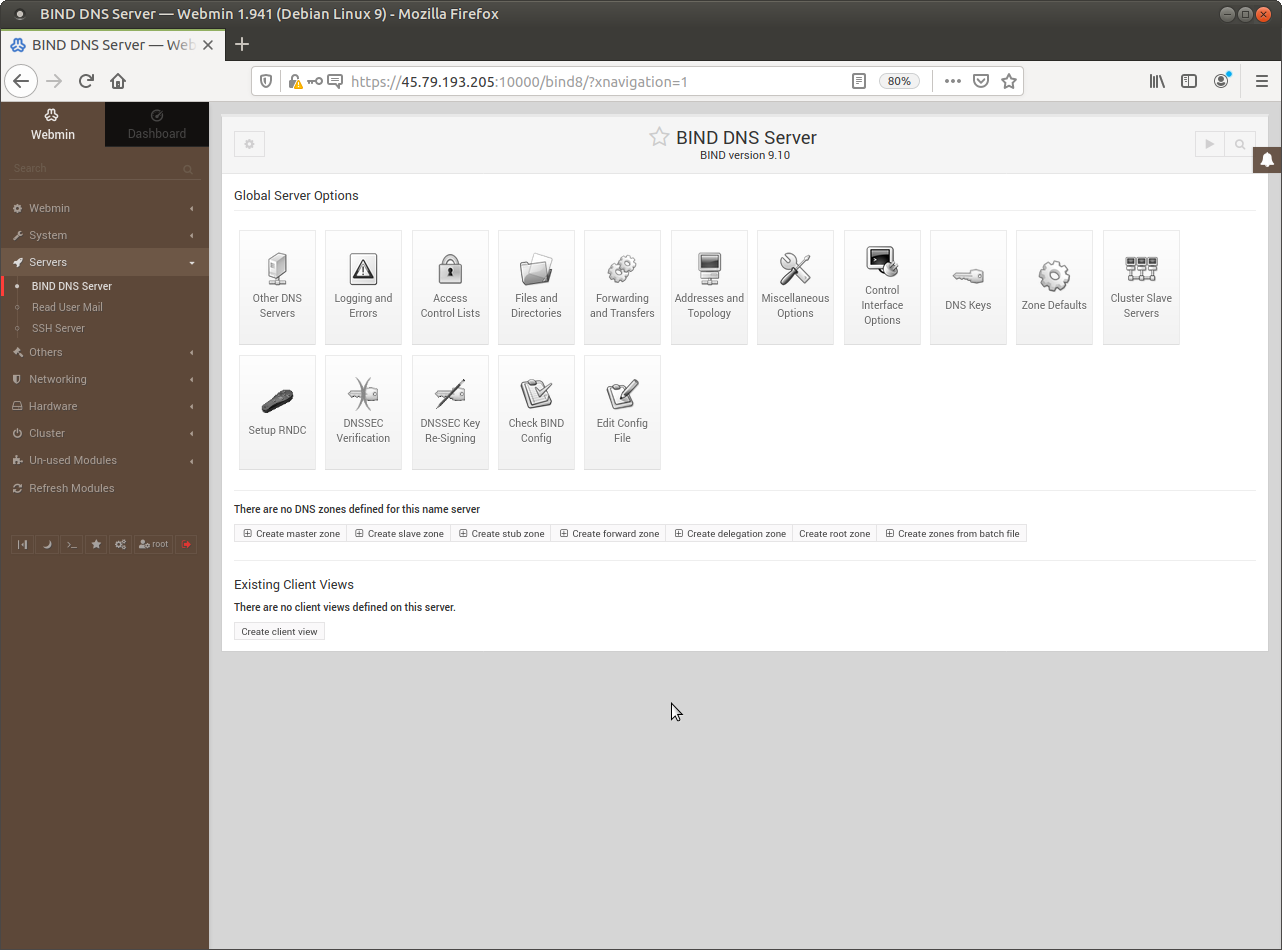 In the upper left corner the icon that looks like a gear is the Module Config. In the upper right corner the icon looks like a “Play” button starts the service. When you configure RDC a “Refresh” button is added. Do not yet start it, but lets look at its home directory.
In the upper left corner the icon that looks like a gear is the Module Config. In the upper right corner the icon looks like a “Play” button starts the service. When you configure RDC a “Refresh” button is added. Do not yet start it, but lets look at its home directory.
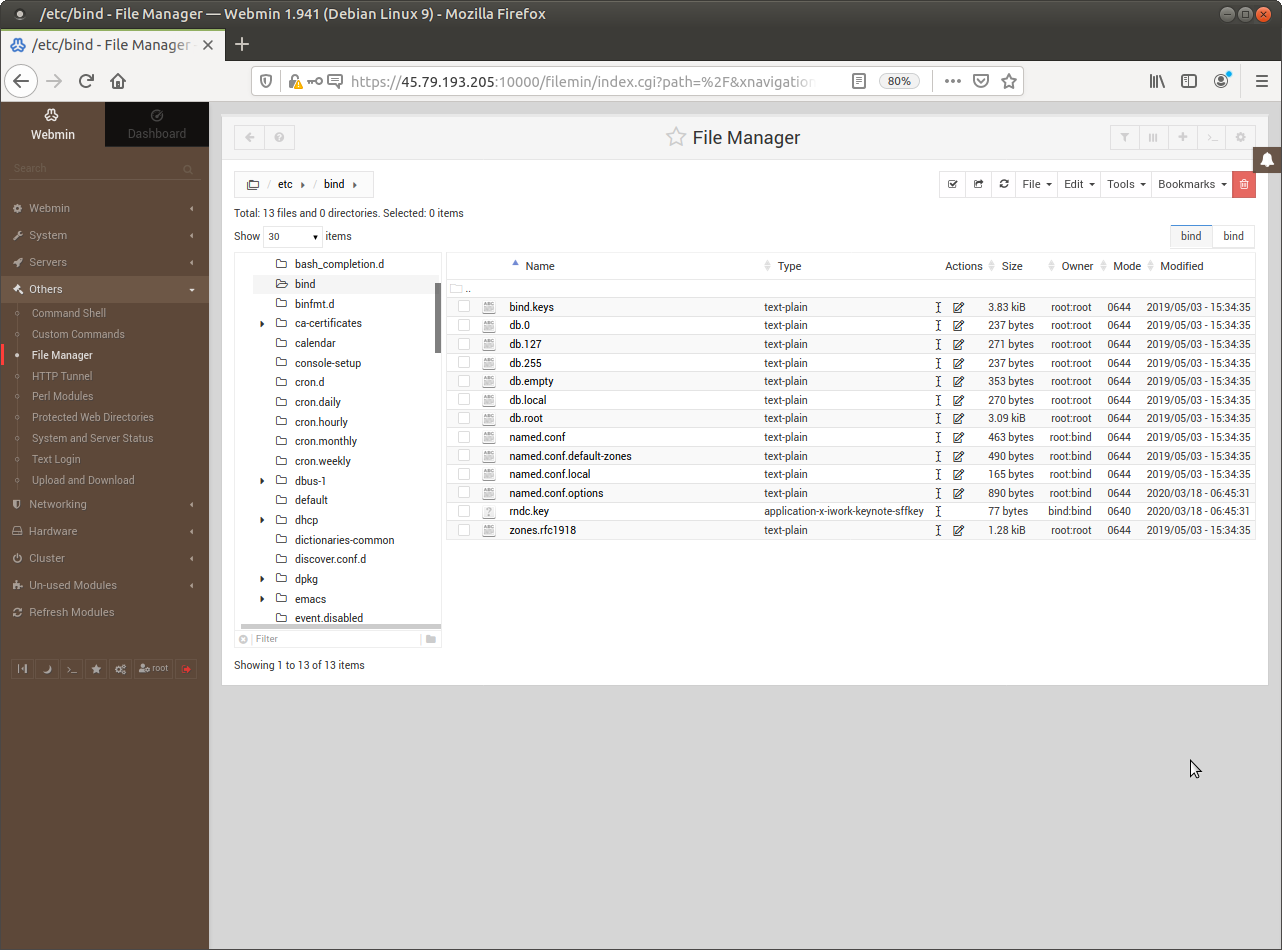 The location and the list of files might be different on a different distribution (Red-Hat, Slackware, or from Enterprises like Oracle).
The location and the list of files might be different on a different distribution (Red-Hat, Slackware, or from Enterprises like Oracle).
Backup and Archive
The difference between backup and archive is the location where they are stored - one is on-line, but going to be lost when the host is lost. The other is off-line, but remains available. These are your choices for backup:
- A manual snapshot by Linode, which you should use for milestones such as before distribution upgrades.
- Three automated backups by Linode, which you should use to recover from errors or attacks.
- A compressed archive by Webmin, which you should use to save parts of the filesystem
- A download / upload utility by Webmin, to keep off-line copies of your archives.
Use the listed above to plan and test your capacity to recover from errors, attacks or even from ransomware. These are very basic, simple measures to keep your service stacks functional.
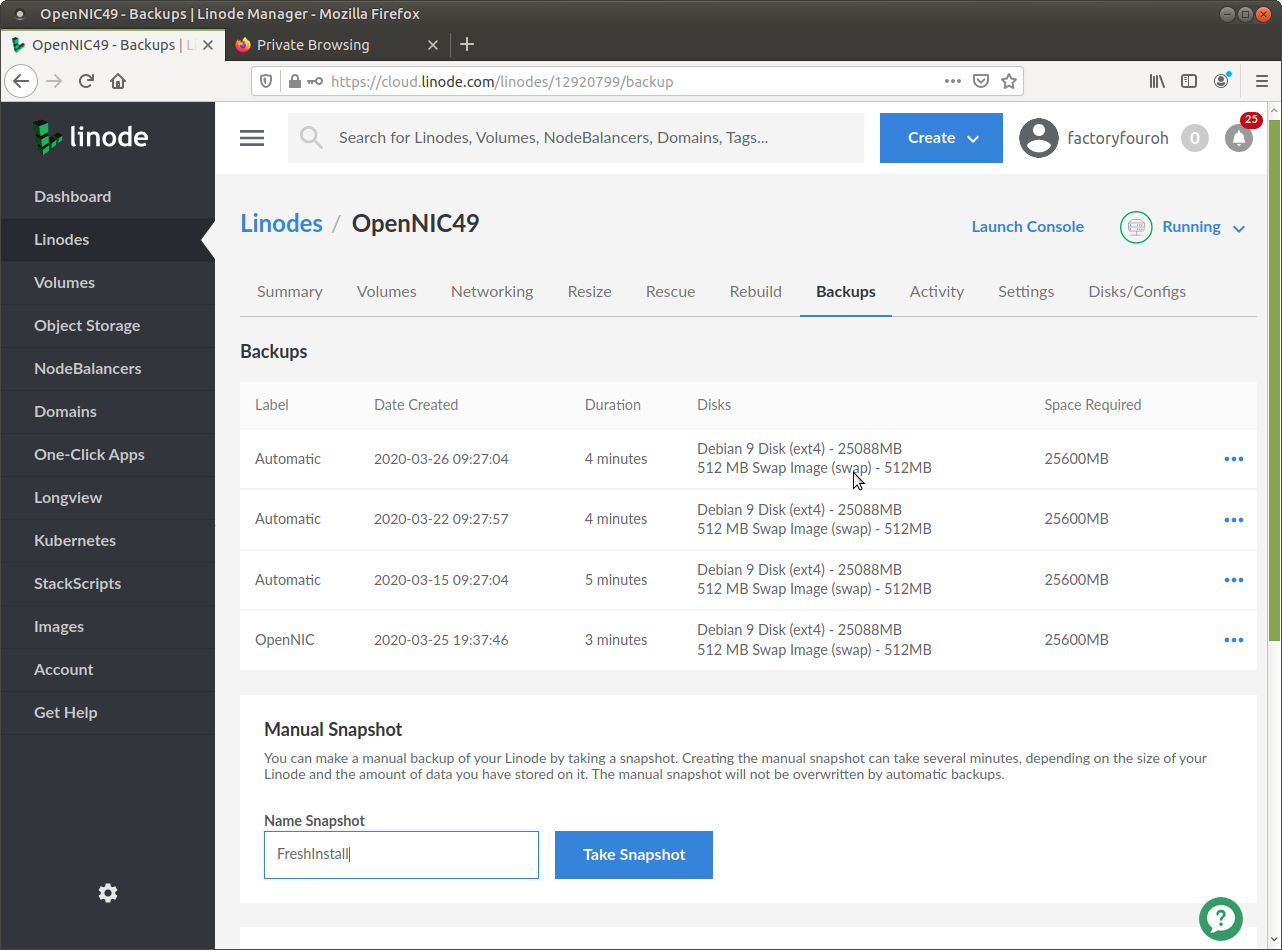 Linode backups and restores never fail, but they replace your ENTIRE instance.
Linode backups and restores never fail, but they replace your ENTIRE instance.
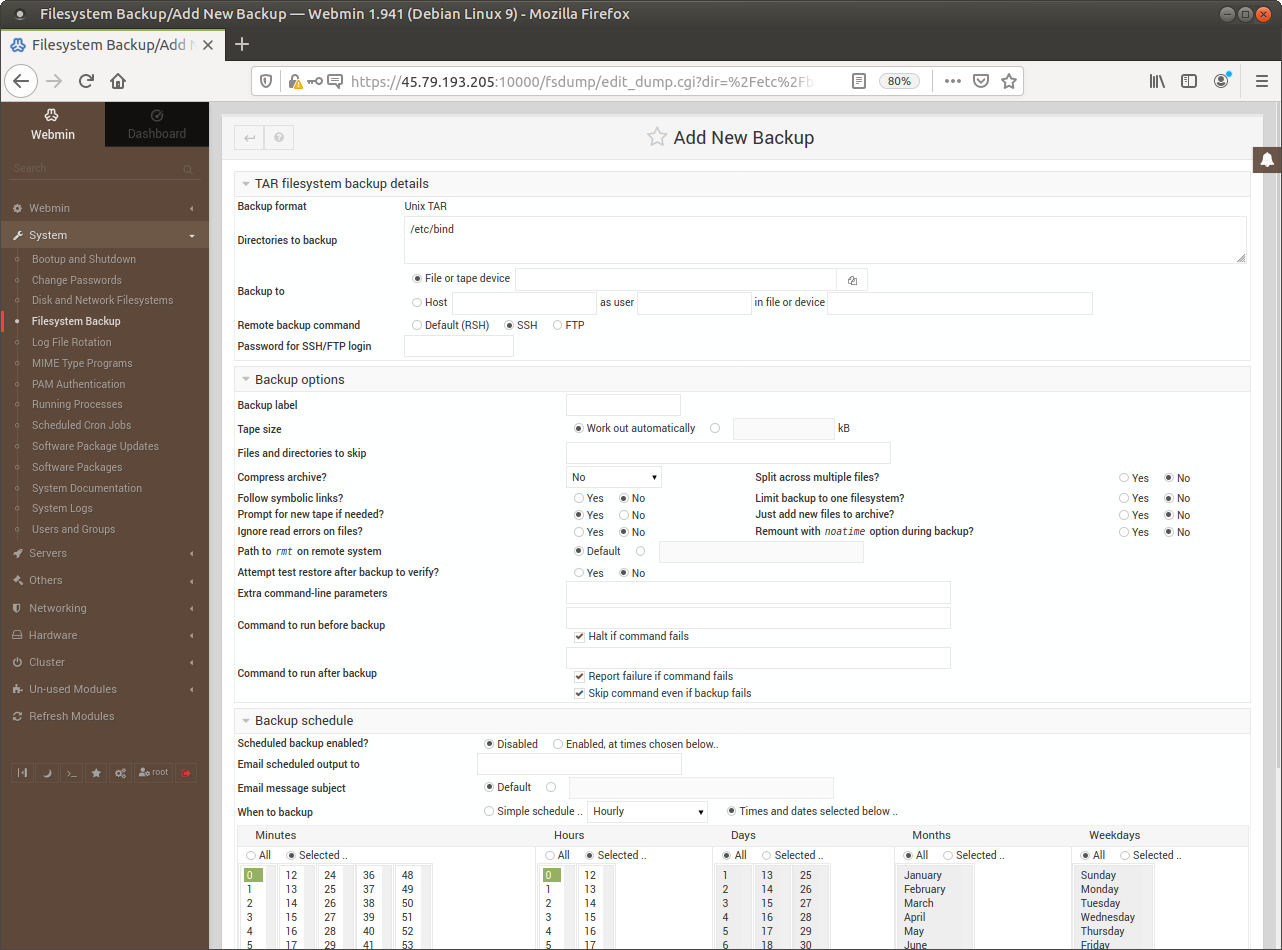 Webmin allows scheduling and creating compressed archives of targeted part of your instance.
Webmin allows scheduling and creating compressed archives of targeted part of your instance.
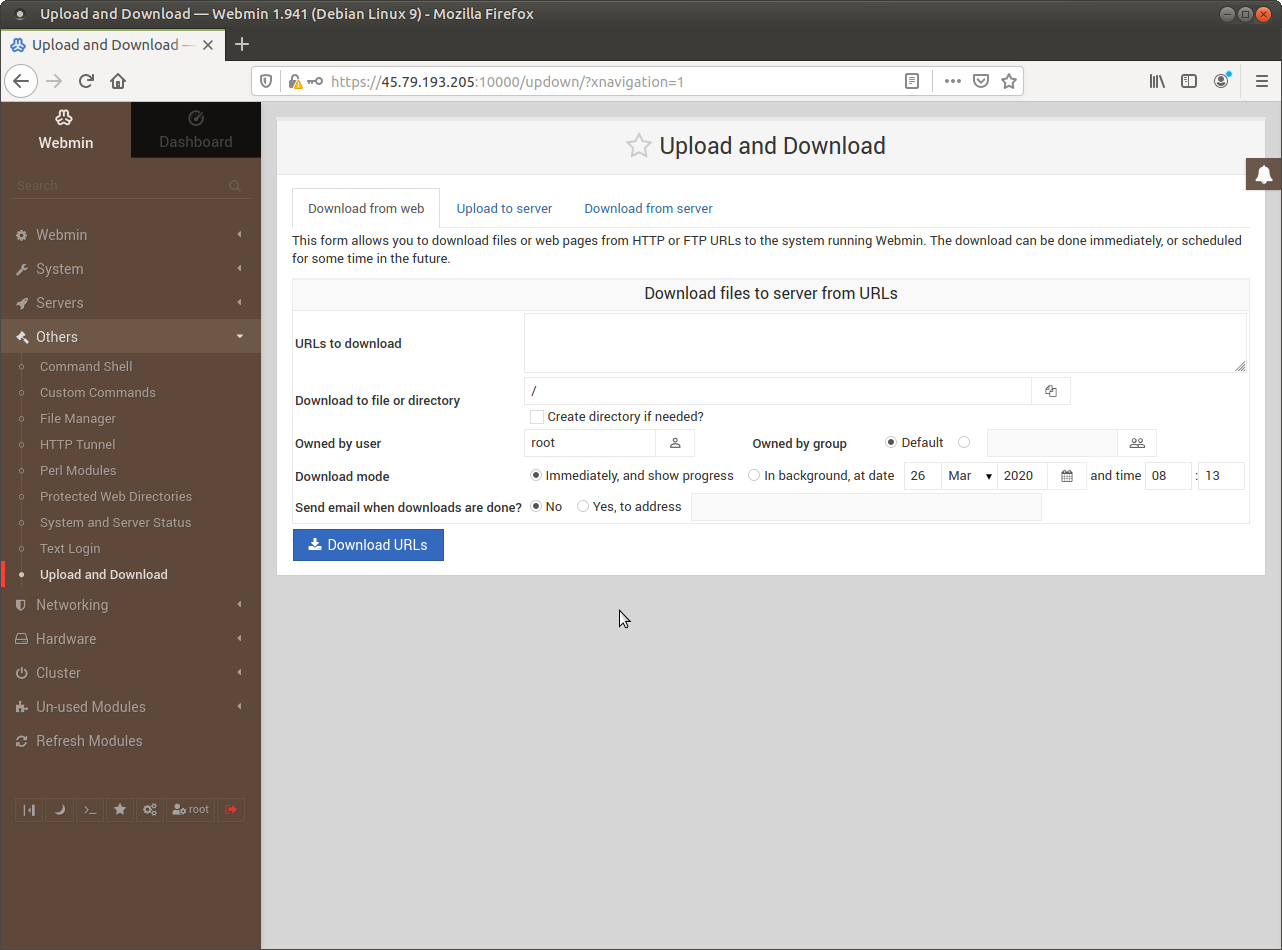 Recover from off-line backup in case of sustained attack going back for weeks or months.
Recover from off-line backup in case of sustained attack going back for weeks or months.
User Management
User management from the shell is expanded by Webmin several ways. The most advanced is Usermin via LDAP, which is not really necessary on single instances. However, using the Webmin Users and Groups modules is necessary to allow login via Webmin - otherwise the user is limited to ssh login only. Also - on production servers Webmin shall not be installed to reduce the number of software exploits.
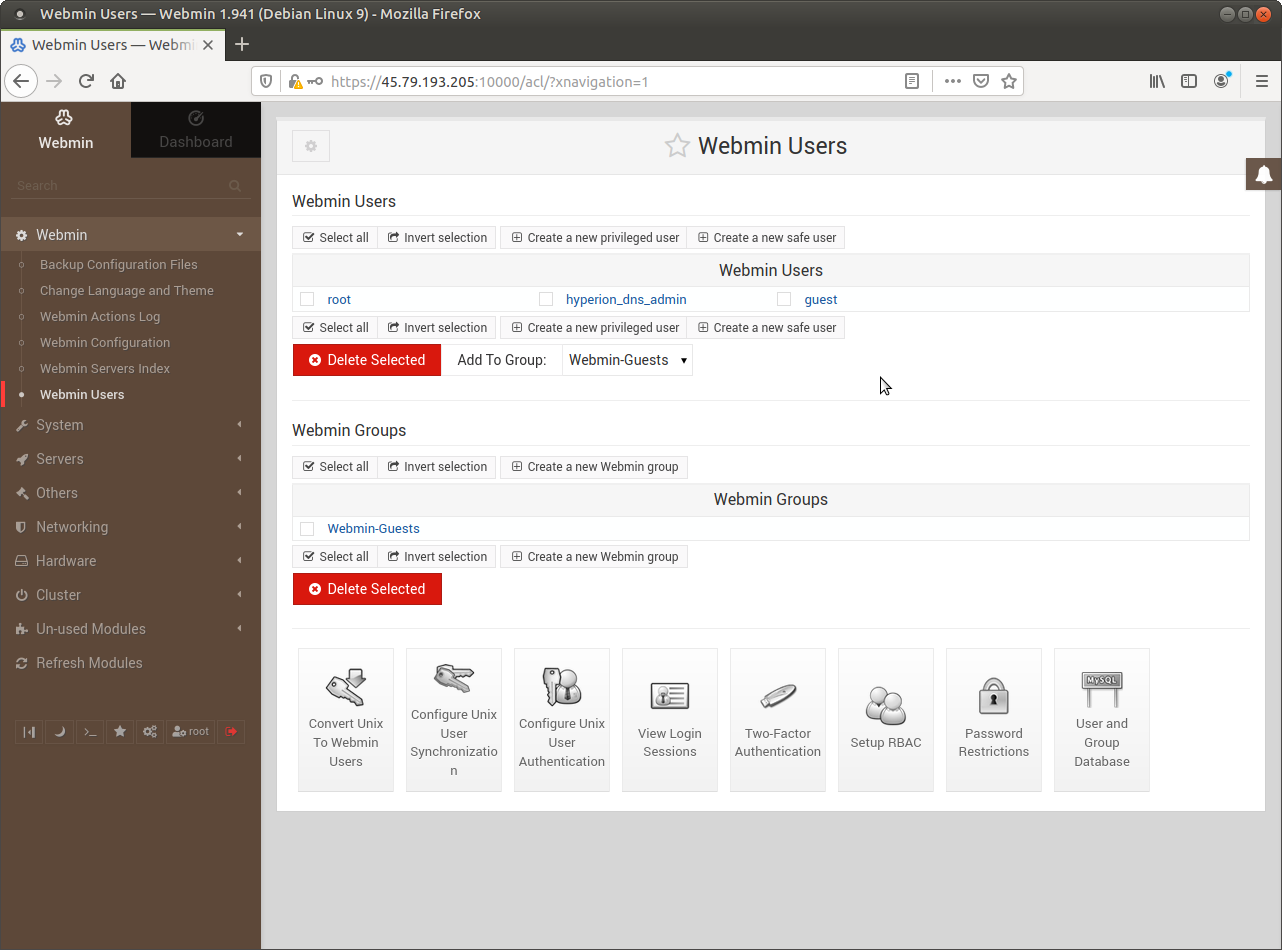 Webmin Users and Groups control access to Modules - but the UNIX user must also exist.
Webmin Users and Groups control access to Modules - but the UNIX user must also exist.
Module Management
These should be the IP4 addresses of the OpenNIC Tier-2s. Normally you use Google's 8.8.8.8 here, but if you enter only that this name-server is NOT going to function. Also note - this is different from the settings of your VPS network, which SHOULD use Google's.
 The DNS administrator has full access to the DNS module and a few others like backup/restore and download/upload.
The DNS administrator has full access to the DNS module and a few others like backup/restore and download/upload.
Network Security
Debian does not assume anything about the purpose of the system, it does not install or configure additional software, and it does not start services by default. iptables is an exception to this, it is installed by default. However, it is not configured and it is not started. If you have installed a firewall software such as FirewallD - iptables is going to be started and managed by that software.
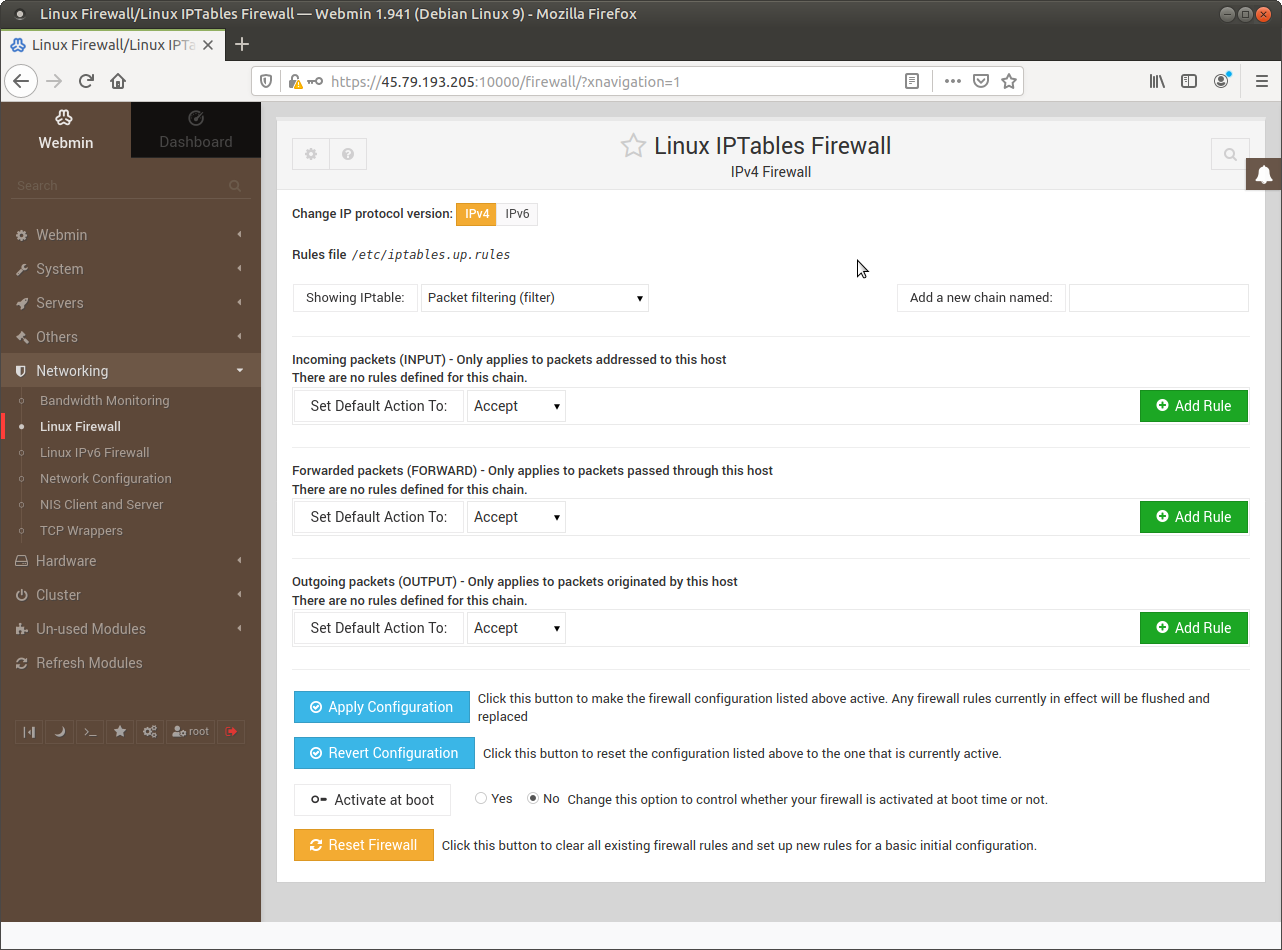 If you start iptables with a wrong configuration you might lose access to your instance!
If you start iptables with a wrong configuration you might lose access to your instance!
Webmin Modules
Some modules in Webmin are matured and well-rounded - the BIND module, for example. Some are obsolete, no longer maintained, and these days they are only included for backwards compatibility - such as the Jabber IM Server. Some are mature and install from within Webmin, some needs to be installed from the shell and tell Webmin to look for them “Refresh Modules”.
 Webmin has good support for FirewallD - but it must be installed from the shell.
Webmin has good support for FirewallD - but it must be installed from the shell.
Logging
Webmin provides access to several logging facilities, with management for logging added for BIND and for Webmin.
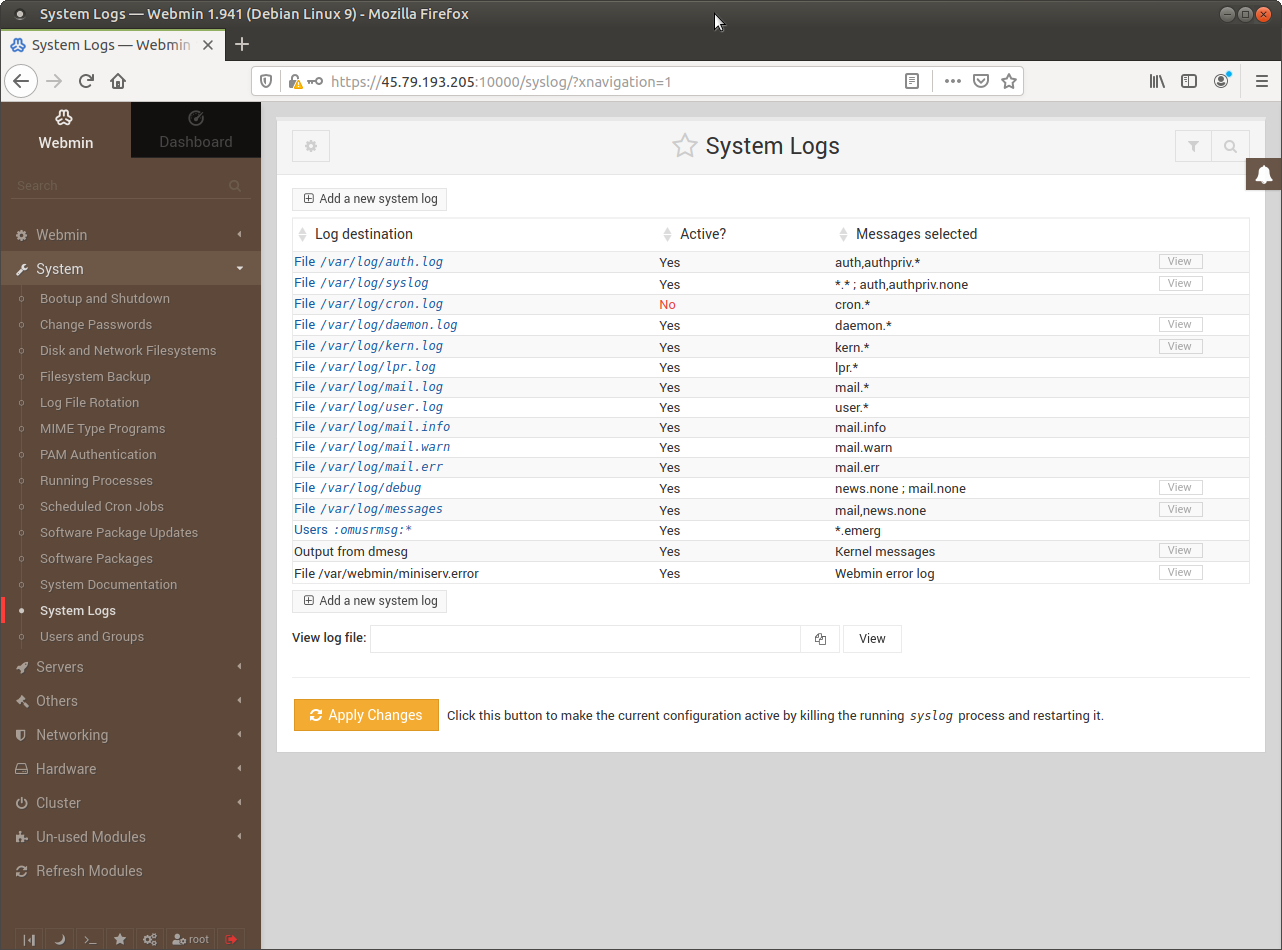 Security starts with these logs, as nearly all attacks leave some clues in these logs.
Security starts with these logs, as nearly all attacks leave some clues in these logs.
Conclusion
You may write your own scripts and use a tool such as Ansible to do more, better than what Webmin does. However, Webmin makes your instances much friendlier inside an environment without Information Technology professionals expert with GNU/Linux. On a factory floor, for example, Webmin is able to serve engineers, managers, production workers with much less training than full-featured but more complex tools.